Services
Audit services of the firm have been designed to support you to meet the challenges involved in managing risks, resources and information.
-
Audit
In our firm we respond to the demands of our customers. We have modern methodologies and audit techniques operating in the best interests of your organization.
-
Statutory Audit
Audit services of the firm have been designed to support you to meet the challenges involved in managing risks, resources and information.
-
External Audit
The external audit service aims to express an independent opinion regarding the fairness of the financia!statements of the companies or certain business areas in which we use previously agreed procedures.
-
Managerial and Result External Audit
Our work consists of the execution of the defined procedures to review the accounting information and issue reports and documents.
Our specialized multidisciplinary team adjust the advice to the customer needs, analyzing the legal alternatives to optimize the use of existing regulations...
-
Taxes
We work with our clients during all their processes to achieve an excellent statutory clase year, in order to optimize the taxes payment and ease the tax burden.
-
Transfer Pricing
The laws surrounding transfer pricing are becoming ever more complex, as tax affairs of multinational companies are facing scrutiny from media, regulators and the public.
-
Legal Services
Our legal advice involves professional lawyers, specialized in different fields.
We have developed a methodology for IFRS process to convert figures and implementation, which has been successfully applied in implemented projects.
-
Diagnosis and implementation of Full and SME IFRS
Servicio de Diagnóstico e implementación de NIIF plenas y NIIF para las PYMES.
-
Training and updating in IFRS
Services of Training and updating in IFRS
-
Calculation of accounting estimates under IFRS
Services of Calculation of accounting estimates under IFRS
-
Valuation of financial instruments
Services of Valuation of financial instruments
-
Advice on specialized topics
Services of Advice on specialized topics
-
IFRS advice for public sector entities
Services of IFRS advice for public sector entities
-
Preparation of financial statements and disclosures
Services of Preparation of financial statements and disclosures
Companies often decide to focus on core business activities, an important reason to choose the outsourcing for other labors. Thereby, the outsourcing improves...
-
Financial accounting
Only those who have clearly structured numbers and a good view of their business, can identify weaknesses and opportunities early enough to react on time to events in their environment.
-
Tax and legal compliance
The tax authorities constantly keep entrepreneurs and freelancers on alert, with tax issues taking part as a crucial role in almost all business decisions.
The Advisory line extends to support companies, in their integration and expansion efforts, with independent services developed by experts, to establish the...
-
Due diligence
Due Diligence is a term, usually used in the field of business acquisitions, to refer to the process of finding information about an organization.
-
Valuations
The valuation of a company is not an exact science and can vary depending on the type of business and the reason.
We have certified experts in security and auditing SAP in R / 3, CRM, BW. Our approach allows us to perform in SAP:
- SAP Implementation Audits
- Functional audit of modules FI, CO, MM, SD, PM, PP, HCM, TM AM
- Evaluation of segregation of functions
- Audit roles, transactions and critical objects in SAP
- Audit of process configuration
- Evaluation of application controls
- Data validation and interface management
- Control of results
- Integrity of the system
- Evaluation of the security architecture
- SAP penetration testing
- Pre-assessment of SAP licensing audits
- Audit of business cycles, developed on SAP
- Performance Tests on SAP
We perform audits on the technological platform that supports SAP, taking into account databases, networks, access architecture, among others.
Methodology
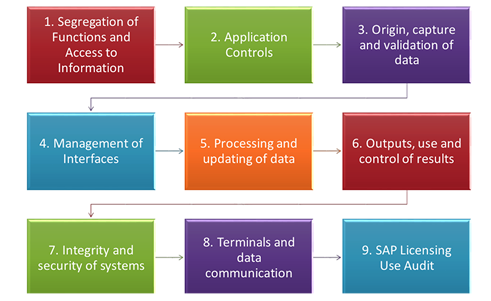 1. Segregation of Functions and access to Information
1. Segregation of Functions and access to Information
- Verify user management policies, standards and supports in SAP
- Check clearly defined role arrays, profiles and users
- Evaluate the documentation of personnel roles of systems for each of the environments (Development, QA and production).
- Evaluate the documentation and control of the system's high impact accounts
2. Application Controls
- Validate that there are controls that support company policies
- Evaluate change management to the application to ensure the integrity and consistency of the information.
- Verify the definition and Control access to third parties
- Evaluation of support service levels in SAP
- Evaluate Service Level Agreements between the Organization and third parties.
- Evaluate user controls and permissions on application transactions.
3. Origin, capture and validation of data
Evaluation of sources such as:
- Control Jobs Bulk uploads
- Non-blocked transactions
- Printing Spooling
- Creating or Modifying Transactions
- Users with Debug permissions
4. Management of Interfaces
- Cross-validation with source
5. Processing and updating of data
- Control of configuration changes
- Review of management activities
- Logging of sensitive activities
- Help Desk (Help Desk)}
6. Outputs, use and control of results
- Evaluate the control of the information that leaves the system
7. Integrity and security of systems
- Security assessment of the platform that supports SAP, networks, servers, databases.
8. Terminals and data communication
- Security on computers that have SAP access
9. SAP Licensing Use Audit
- Determine whether purchased licenses are being properly exploited
Read more
